KEY POINTS FROM THIS ALERT:
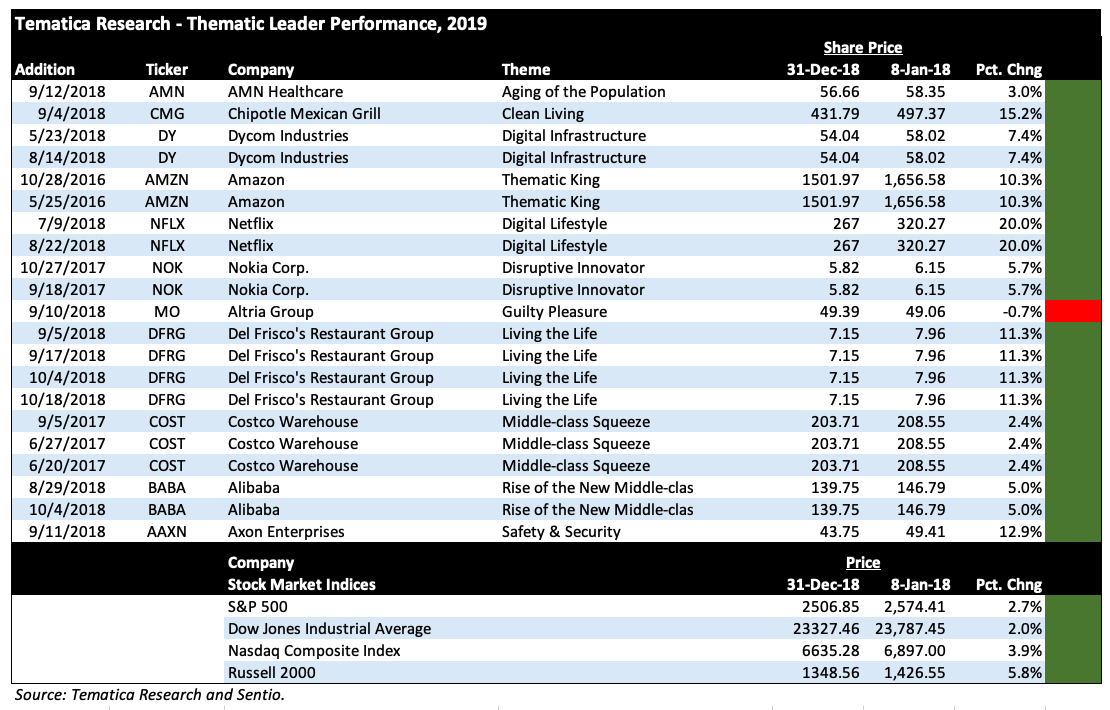
- We are issuing a Buy on Axon Enterprises (AAXN) and adding them to the Tematica Investing Select List with a $90 price target.
The right to defend yourself and your property apply in today’s increasingly connected world, just as it did more than 200 years ago. While the public debate and much of the media coverage focus on the Second Amendment and the right to keep and bear arms, the threats we face today are changing, just as the way we interact with people, data and content are changing. As individuals, companies and countries, we must be increasingly on guard and behaviors need to shift away from reactionary defense towards always prepared and secure, much the way we’ve seen with homeland security and traditional national defense.
Tematica’s Safety & Security investing theme looks to tap into evolving needs across individual, cyber, corporate and homeland security. In turn, the Safety & Security Index targets companies that offer products and services across that range, from corporate security and monitoring solutions, to personal firearms arms and home-security, to individual, corporate and national cyber security to defense spending.
It wasn’t too long ago that the WannaCry and Petya cyber-attacks dominated the headlines. Over the past few years, cyber security we have seen a significant increase in the number of cyber-attacks plaguing individuals, corporations and other institutions across the globe. In our view, there is little cybersecurity is a growth market as individuals, companies and other institutions look to ward off future attacks, shore up their existing cyber defenses, assess attack and intrusion analytics and become far more secure.
We see this reflected in the forecasts calling for cybercrime to cost $6 trillion annually by 2021, up from $3 trillion in 2015 according to Cybersecurity Ventures. From a somewhat different perspective, in the five years ending in 2021, worldwide spending on cyber security software, services, and hardware services is expected “to eclipse $1 trillion”. As one might expect one of the fastest growing tech categories through 2021 will be managed security services with CAGR 14.7%, according to International Data Corporation.
Here’s the thing, as crucial as cybersecurity will be in the coming years, it is still just one aspect of the far larger amount of spending that occurs each and every year to keep our nation, businesses, homes and families safe.
Case in point, total global cyber security spending represented roughly 23 percent of the $522 billion 2017 U.S. defense budget. Candidate Trump pledged to rebuild the US military and President Trump is looking to boost defense spending to $716 billion in 2019, a 10 percent increase from the amounts set for the Department of Defense in the continuing resolutions levels. Over the 10-year budget window, funding for the Department of Defense is $1 trillion above projections from the previous administration. In addition to big-ticket items like military aircraft, ships and other marine vessels, the budget includes national security spending, cyber defense, weapons procurement, as well as research and procurement.
Keep in mind that is just at the federal level. At the local and state level, we are seeing shifts in spending by law enforcement to more Disruptive Innovator led solutions such as body cameras and tasers to name a few. According to QY Market, the global market for body cameras is expected to reach about $1.5 billion by 2021 from $259.5 million in 2016. Forces driving the growth in the body camera market include the growing demand for monitoring police conduct as well as transparency in evidence collection and handling. The non-lethal weapons market comprised of military and law enforcement is estimated to reach $8.4 billion by 2020, a CAGR of 8.2 percent from 2015 to 2020.
Outside the US, rising global tensions have led to increasing demand for defense and military products in the Middle East, Eastern Europe, North Korea, the Far East and South China Seas. This is, in turn, instigating increased defense spending globally, especially in the United Arab Emirates (UAE), Saudi Arabia, South Korea, Japan, India, China, Russia. For example, the Middle Eastern Homeland Security market is slated to grow at a CAGR of 15.5 percent to achieve $17.05 billion by 2021, up from $7.19 billion in 2015, driven by government initiatives to create a smart and secure environment amidst high terrorist activities in the region.
Protections Gets Personal
With the media’s emphasis on cyber security (just Google “security” and see what comes up), attention is lost on other aspects of individual or personal security. The global home security solutions market, (which includes video surveillance, electronic locks, alarms, access control, sensors, detectors and corresponding services) is predicted to reach $30.3 billion by 2022, up from $8.3 billion in 2014.
The increasing acceptance of video surveillance systems is expected to propel the video surveillance sub-sector in the years to come with demand for IP-based video surveillance expected to increase due to its improved video capturing quality. This growth is not just U.S.-based as the number of monitored alarm systems in Europe is forecast to grow from 8.7 million in 2016 to reach 10.6 million in 2021, according to a new research report by Berg Insight. By comparison, in North America, the number of monitored alarm systems is forecasted to grow from 32.1 million at the end of 2016 to 37.1 million at the end of 2021.
THE SAFETY & SECURITY TAILWINDS
As much as the Safety & Security investment theme is demand-driven as people, corporations, governments and other entities spend on protecting and securing themselves, it is one that is ripe for change as industries evolve and in some cases embrace our Digital Lifestyle and Digital Infrastructure themes. Just one case in point, the M&A activity in the defense contracting sector for cyber firms as the “battlefield” increasingly expands into the virtual world.
Another component arises when we look to the Internet of Things (IoT) and the increasing reality that even our own personal possessions could be rendered useless through a cyberattack unleashed by a foreign government or other entity. In 2015 for example, Black Hat hacked a 2014 Jeep Cherokee over the internet and paralyzed it on I-64 forcing Chrysler to recall 1.4 million vehicles. Hackers have found security flaws in smart home connectors that are used to turn up the thermostat, turn on your lights or access your Wi-Fi network through your smart fridge.
It’s this reality that the Tematica Safety & Security investing theme taps into as it covers the full range of companies participating in the security and monitoring of our homes, families, companies and homeland.
Axon Enterprise – Not just Taser anymore
Given the wide lens of our Safety & Security theme, there are many companies to consider, but the one we are focusing on is Axon Enterprises, the company formerly known as Taser, of which most of us have heard. Why the name change? Odds are there were several reasons, but the most poignant one is the transformation of the company’s business model from one predicated on conducted electrical weapons (CEW), better known as Tasers, to a more balanced one between those weapons and connected wearable on-officer cameras (Axon), an in-car camera variant (Axon Fleet) and complimentary cloud-based digital evidence management software (Evidence.com). Evidence.com is the company’s data management system, chain-of-custody controls and security protocols that law enforcement agencies use to preserve and protect data from body cameras and in-car video systems.
There are several reasons why we like that transformation. The company now has more diversified business model and one that has aspects of recurring revenue streams that tend to receive more favorable valuation multiples, compared to the 15x-19x earnings at which firearm companies American Outdoor Brands (AOBC; formerly Smith & Wesson), and Sturm, Ruger & Company (RGR) are trading at based on expected 2019 EPS. There is also the replacement cartridge aspect of CEW weapons, which is very similar to ammunition in that continued replenishment is required, which results in an on-going revenue stream. Currently, munitions company Vista Outdoors (VSTO) is trading at 36x expected 2019 earnings.
As we touched on above, the outlook for the domestic body camera market looks vibrant over the next several years, and that augurs for growth for corresponding digital records management solutions. Easing Axon’s entrance into this market and the transformation in its business model is its existing relationship with more than 20,000 public safety agencies worldwide that span law enforcement, corrections, and military forces as well as private security personnel and in the case of its CEWs, private individuals. At the end of 2017, 38 of the top 50 metropolitan areas in the U.S. were on the Axon network.
Strengthening Axon’s position in the body camera and digital storage markets was its May 2018 acquisition of VIEVU, a body camera and cloud-based evidence management system competitor. That acquisition expanded Axon’s customer base to include among others the New York City Police Department, the Miami-Dade Police Department, the Phoenix Police Department, the Oakland Police Department and the Aurora, CO Police Department as well as Mexico City and Mexico’s federal police. Given the timing of the acquisition, it had a modest impact on the June 2018 quarter, but should be a greater contributor over the coming quarters from a revenue and cost synergy perspective as Axon integrates its customers and platforms.
In June, Axon reached a partnership with Milestone Systems, a leading open platform IP video management software provider, that brings data from more than 6,000 models of cameras from 150 manufacturers, including CCTV footage, into Evidence.com. As with other data stored in Evidence.com, this new data will be trackable, easily shareable, and redactable.
Also, in the first half of 2018, Axon inked a strategic partnership with drone manufacturer DJI to sell its video-capable drones directly to police officers through a new Axon Air program. More than 900 American public safety agencies use drones to improve officer safety, support tactical actions, reconstruct traffic collisions, support public safety at large events and perform search-and-rescue missions. Axon’s strategy is to leverage its police and law enforcement customer base to sell the DJI drones bundled with access to Axon’s connected data network and Evidence.com services.
Exiting the June 2018 quarter, the company’s install base included 450,000 Tasers in the U.S, an active camera count of more than 300,000 and a growing subscription business at Evidence.com. While the bulk of the company’s business is inside the U.S., roughly 20% of its CEW business is international with fresh opportunities in both the UK and Italy. Based on the company’s current market share as well as recent moves to expand its reach with its VIEVU acquisition and partnership with DJI, Axon is well positioned to ride the expanding tailwind that is the body camera and digital support market. Exiting 2017 the global body-worn camera shipment market was 1.05 million units, up from 0.17 million, and is forecasted to reach 1.59 million units this year and more than 5.6 million units in 2021. While the US is the largest body camera market today, the adoption of body-worn cameras by the police officers in Europe region is growing and that is expected to be followed by Asia-Pacific in the coming years.
Following the completion of a 4 million share equity offering this past May that raised roughly $245 million in capital, Axon’s balance sheet had net cash of $311.6 million ($5.35 per share). Combined with its positive cash flow from operations, the company has ample funding to pursue other strategic initiatives, including additional acquisitions and alliances, to expand its business in both the domestic and international markets. Per the company, it sees its total addressable market in the near term as $7.7 billion, which breaks down to $1.5 billion in TASER weapons, $0.7 billion in hardware sensors/body cameras and $5.5 billion in cloud-based public safety software. Even if we were to annualize Axon’s June 2018 revenue, which would clock in at just under $400 million vs. the $344 million achieved in 2017, there are ample share gains to be had in this expanding market that are expected to drive its EPS to $1.07 in 2020, up from $0.52 this year and $0.27 in 2017.
Inherent in those EPS expectations is for its Software and Sensors business segment to turn from one generating operating losses to profits. In the first half of 2018 quarter, all of Axon’s operating profits were derived from its Taser business while Software and Sensors reported an operating loss of $16.9 million on $76 million in revenue. In comparing that time period with the first half of 2017, we see the Software and Services business made considerable ground in reducing the drag on the company’s overall profits as segment revenue continued to climb. For the first half of 2017, Axon’s Software and Sensor business reported an operating loss of $31.6 million on revenue of $48.2 million. Crunching the year over year change in operating losses vs. revenues tells us the Software and Sensor business achieved incremental operating margins of 52.5% in the first half of 2018, a very positive sign that says for every incremental revenue dollar, the company was earning $0.52 in operating profit. In other words, the likelihood that Software and Sensors becomes a profit generator in the coming quarters is rather high. Our analysis suggests the break-even level for the business is around $220-240 million in annual revenue vs. the annualized first half of 2018 level near $153.6 million and $96.4 million for the first half of 2017.
If there were one bone to pick with Axon, it would be the stock’s current valuation, which sits at a P/E ratio of more than 65x expected 2020 EPS of $1.07 and an eye-popping 102x consensus forecasted $0.69 in 2019. When faced with such robust valuations, we recognize the danger of solely focusing on a stock’ P/E ratio if one does not account for the underlying EPS growth. Hence our usage of the price-earnings to growth ratio for Amazon (AMZN) and here with Axon shares. Over the 2017-2020 period, Axon is forecasted to grow its EPS at a compound annual growth rate (CAGR) of 157%. Granted this slows to roughly 143% for the 2018-2020 time frame from 160% over the 2017-2019 period, but even if we utilize that slower growth rate it means Axon shares are trading at a steep discount on PEG basis using either 2019 or 2020 EPS expectations.
While it can be tempting to get all “pie in the sky” with that valuation potential, it does point to upside in the shares near $100-$110 if Axon delivers on the consensus 2019 EPS forecast with a PEG multiple of just 1.0x, we have to consider a potential profitability timing slip with Axon’s Software and Sensor business. This could impact EPS expectations, so to be conservative we’re haircutting both the company’s EPS CAGR and expected EPS in 2019 and 2020.
Applying either . . .
- An EPS CAGR rate of 140% on potential 2019 EPS of $0.65 with a PEG ratio of 1.0 or
- A 0.9 PEG ratio to an EPS CAGR of 145% on potential 2019 EPS of $0.69
. . . and both deliver a price target of $90. If Axon’s can hit the expected growth trajectory through 2020, a similar analysis implies upside to more than $130.
Yes we know, quite the math-Olympics in that last paragraph, but those efforts reveal upside of at least 28% from current levels over the coming year. On the downside, AAXN shares have bottomed out at an average of 58.5x forward earnings over the 2016-2018 period, which suggests downside to just over $60. That’s potential downside of 14%, which means net upside vs. downside in the shares over the coming year, on a conservative basis is 14%.
Recognizing the strong likelihood for continued adoption of its Software and Services business that will drive its business transformation, we are adding shares of Axon Enterprises (AAXN) to the Tematica Investing Select List with a $90 price target over the 15 months. Based on the company’s ability to wring profitability out of this business segment, we’ll look to revise that target in the coming months. Should AAXN shares come under pressure, all things being equal we would look to scale into the shares closer to $60.
As we monitor the position, we’ll continue to watch the further adoption of body cameras and Evidence.com by existing customers as well as new ones. We’ll also be keeping tabs on the patent litigation against Axon from competitor Digital Ally (DGLY), which has the date of January 16, 2019 for its Final Pretrial Conference. With a market cap of $20.4 million and roughly $11 million in net cash following a recent $10 million equity infusion, one way for Axon to remove this concern would be to utilize its balance sheet in a move that would further shore up its competitive position.
- We are issuing a Buy on Axon Enterprises (AAXN) and adding them to the Tematica Investing Select List with a $90 price target.
Companies riding the Safety & Security tailwind:
- American Outdoor Brands (AOBC)
- Carbonite (CARB)
- Check Point Software (CHKP)
- Cisco Systems (CSCO)
- F5 Networks (FFIV)
- Fortinet (FTNT)
- General Dynamics (GD)
- Imperva (IMPV)
- Lockheed Martin (LMT)
- Northrop Grumman (NOC)
- OSI Systems (OSIS)
- Palo Alto Networks (PANW)
- Proofpoint (PFPT)
- Qualys (QLYS)
- Raytheon (RTN)
- Science Applications International Corp. (SAIC)
- Sturm, Ruger & Co. (RGR)
- Verisign (VRSN)
- Vista Outdoor (VSTO)